
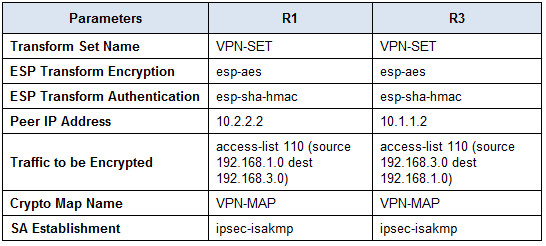
8.4.1.3: Configure a Site-to-Site VPN Using CLI: MAP w/ASA or MAP: Lab versions provided for both the ASA 5505 and 5506. 9.3.1.2: Configure ASA Basic Settings and Firewall Using CLI: MAP w/ASA: Lab versions provided for both the ASA 5505 and 5506. 10.1.4.8: Configure ASA Basic Settings and Firewall Using ASDM: MAP w/ASA. Navigate to Configuration Site-to-Site VPN Advanced ACL Manager The table of ACLs defined on the ASA appears. Click Add Add ACL. Enter the name Site1-VPN-Filter and click OK. CCNA Security 2.0 Labs: 8.4.1.2 Packet Tracer - Configure and Verify a Site-to-Site IPsec VPN using CLI Answes completed free download.pka file completed. IKEv2 was introduced in version 8.4 so we have had this for a while. (This is an 11 year old post!) IKEv1 Cisco ASA Site To Site VPN IKEv1 'Using CLI' IKEv2 Cisco ASA Site To Site VPN IKEv2 'Using CLI'.
8.4 1.3 Lab Site To Site Vpn Using Cli Chrome
8.4 1.3 Lab Site To Site Vpn Using Cli Commands
A common requirement with Site-to-Site tunnels is access-control through the tunnel. Godus wars. One strategy to accomplish this might be to have a rather complex crypto ACL. But this leads to additional administration overhead as there is actually a pair of IPsec SAs for each active
entry in the crypto ACL. The proper way to limit traffic through a Site-to-Site tunnel with the ASA is to apply a filter via group policy. In this section of the lab, you will prevent Site1 systems from reaching the management subnet.
1. Create an ACL which denies access to 10.10.2.0/24 for use as a filter for the Site1 VPN
Navigate to Configuration > Site-to-Site VPN > Advanced > ACL Manager
The table of ACLs defined on the ASA appears.
Click Add > Add ACL.
Enter the name Site1-VPN-Filter and click OK.
With Site1-VPN-Filter highlighted in the table, click Add > Add ACE.
Define the first Access Control Entry as follows:
• Action: Deny
• Source: Any
• Destination: 10.10.2.0/24
• Service: ip
Leave other options at their default values and click OK.
Select the first line in the Site1-VPN-Filter and select Add > Add ACE.
Define the first Access Control Entry as follows:
• Action: Permit
• Source: Any
• Destination: Any
• Service: ip
Leave other options at their default values and click OK.
Click Apply. Terraria 1.3.4 download free.
2. Modify the group policy for Site1-VPN, and select the new ACL as the filter:
Navigate to Configuration > Site-to-Site VPN > Group Policies
Select the Site1-Policy and click Edit.
Modify the group policy as follows:
• IPv4 Filter: Uncheck Inherit and select Site1-VPN-Filter
Leave the other values at their defaults and click OK.
Click Apply.
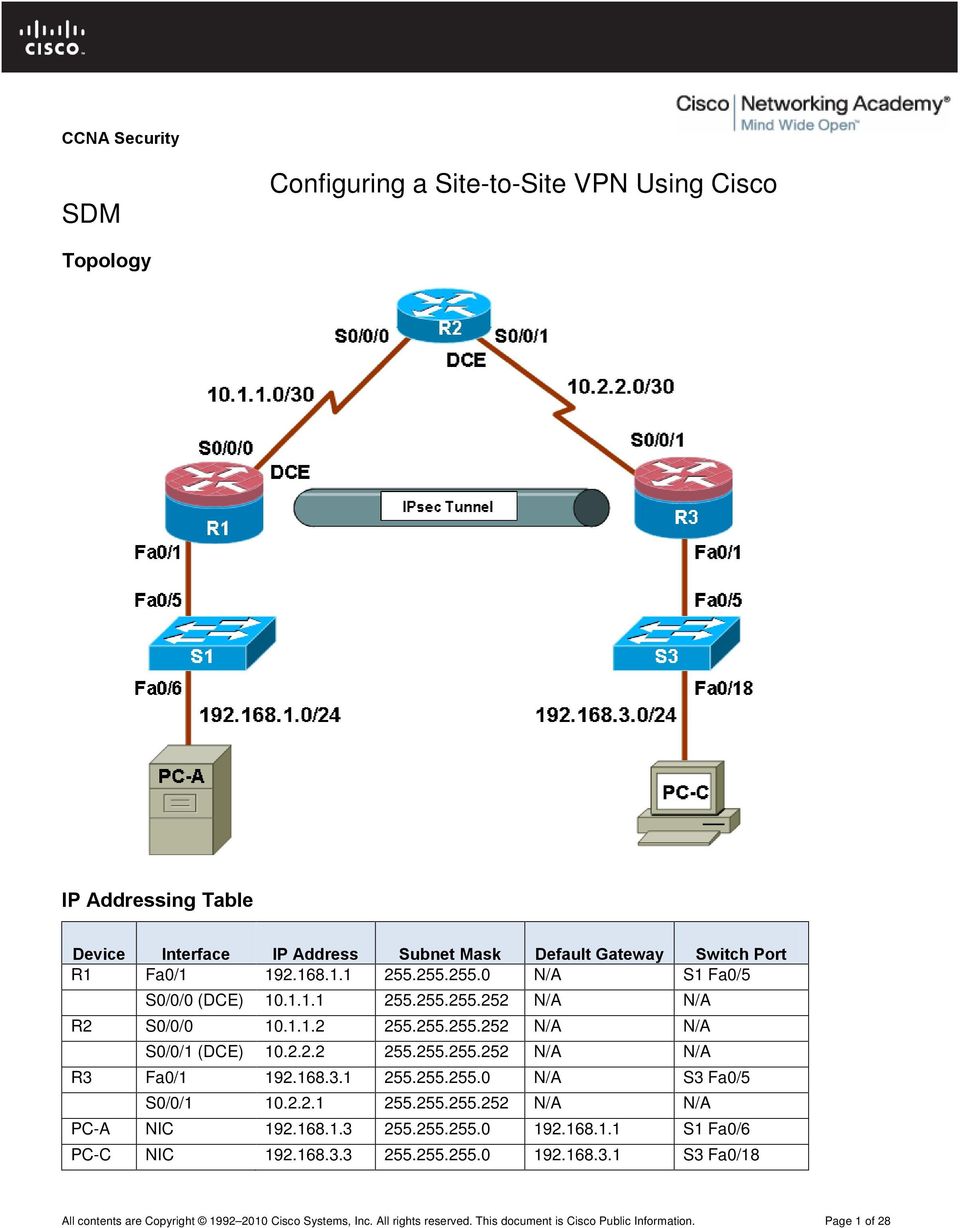
8.4.1.3: Configure a Site-to-Site VPN Using CLI: MAP w/ASA or MAP: Lab versions provided for both the ASA 5505 and 5506. 9.3.1.2: Configure ASA Basic Settings and Firewall Using CLI: MAP w/ASA: Lab versions provided for both the ASA 5505 and 5506. 10.1.4.8: Configure ASA Basic Settings and Firewall Using ASDM: MAP w/ASA. Navigate to Configuration Site-to-Site VPN Advanced ACL Manager The table of ACLs defined on the ASA appears. Click Add Add ACL. Enter the name Site1-VPN-Filter and click OK. CCNA Security 2.0 Labs: 8.4.1.2 Packet Tracer - Configure and Verify a Site-to-Site IPsec VPN using CLI Answes completed free download.pka file completed. IKEv2 was introduced in version 8.4 so we have had this for a while. (This is an 11 year old post!) IKEv1 Cisco ASA Site To Site VPN IKEv1 'Using CLI' IKEv2 Cisco ASA Site To Site VPN IKEv2 'Using CLI'.
8.4 1.3 Lab Site To Site Vpn Using Cli Chrome
8.4 1.3 Lab Site To Site Vpn Using Cli Commands
A common requirement with Site-to-Site tunnels is access-control through the tunnel. Godus wars. One strategy to accomplish this might be to have a rather complex crypto ACL. But this leads to additional administration overhead as there is actually a pair of IPsec SAs for each active
entry in the crypto ACL. The proper way to limit traffic through a Site-to-Site tunnel with the ASA is to apply a filter via group policy. In this section of the lab, you will prevent Site1 systems from reaching the management subnet.
1. Create an ACL which denies access to 10.10.2.0/24 for use as a filter for the Site1 VPN
Navigate to Configuration > Site-to-Site VPN > Advanced > ACL Manager
The table of ACLs defined on the ASA appears.
Click Add > Add ACL.
Enter the name Site1-VPN-Filter and click OK.
With Site1-VPN-Filter highlighted in the table, click Add > Add ACE.
Define the first Access Control Entry as follows:
• Action: Deny
• Source: Any
• Destination: 10.10.2.0/24
• Service: ip
Leave other options at their default values and click OK.
Select the first line in the Site1-VPN-Filter and select Add > Add ACE.
Define the first Access Control Entry as follows:
• Action: Permit
• Source: Any
• Destination: Any
• Service: ip
Leave other options at their default values and click OK.
Click Apply. Terraria 1.3.4 download free.
2. Modify the group policy for Site1-VPN, and select the new ACL as the filter:
Navigate to Configuration > Site-to-Site VPN > Group Policies
Select the Site1-Policy and click Edit.
Modify the group policy as follows:
• IPv4 Filter: Uncheck Inherit and select Site1-VPN-Filter
Leave the other values at their defaults and click OK.
Click Apply.
The policy is defined, but it won't take effect until the next time the Site1 VPN tunnel is negotiated.
3. 'Bounce' the Site1 tunnel:
Navigate to Monitoring > VPN > VPN Statistics > Sessions
Set the filter to IPsec Site-to-Site.
If the tunnel to 200.200.20.2 is still active, click Logout.
Here you can download file tally72migration. 2shared gives you an excellent opportunity to store your files here and share them with others. Join our community just now to flow with the file tally72migration and make our shared file collection even more complete and exciting. Download the tool tally72migration.exe and save it in the Tally ERP 9 installation folder.; Run the Tally ERP 9 Data Migration Tool. Tally ERP 9 will also open in a separate window. You will see the message Ready for Migration in the Migration Messages panel.; Select Migrate Data, and specify the data path. Select the company from the List of Companies. Migrate data from Tally 5.4, 6.3 and 7.2 to Tally.ERP 9 To migrate data from releases below Tally.ERP 9, you need the migration tool tally72migration.exe that is available in Tally.ERP 9 installation folder. Before migrating data, it is recommended that you backup your data. Tally 72 migration tool download. The word 'crack' in this context means the action of removing the copy protection from commercial software. A crack is a set of instructions or patch used to remove copy protection from a piece of software or to unlock features from a demo or time-limited trial.
Posted in ASA Site-to-Site VPN, Network Security
